Stay safer online with two-factor authentication

In a well-intentioned effort to help us stay safer online, most online sites and services that involve a login to protect sensitive or personal data and information are now encouraging or even insisting on the use of complex passwords involving various combinations of upper- and lower-case letters, punctuation and like. Most people are happy to oblige and understandably assume that their log-in is secure and at least somewhat more un-hackable from that point forward.
But is that assumption valid?
While we would never discourage anyone from using a complex password, the reality is that any single factor authentication scheme, such as one based solely on username and password – no matter how complex – represents a fairly low bar for savvy cyber criminals. A far more secure approach involves two-factor or multi-factor authentication. In this approach, logging in requires something you know (i.e. password and username) and something you have, such as a code sent to your phone via a text message.
As you might imagine, a two-factor process can help to lower the number of cases of identity theft and their impact, as well as phishing via email, because criminals need more than just name and password details.
The challenge with multi-factor authentication is complexity. The traditional solution in enterprise environments has involved RSA SecureID hardware tokens and supporting security infrastructure. While effective and well-proven, this technology is rarely seen outside the large enterprise world. It’s expensive and needs IT support to implement.
Most larger consumer and social media sites now offer a variety of two-factor authentication options. Like most sites, Facebook for instance, as shown below, doesn’t enable two-factor authentication by default but does offer a range of options for users consider for improved security. If you use Facebook to log-in to other sites beyond Facebook itself, definitely take a few minutes to set up two factor authentication.
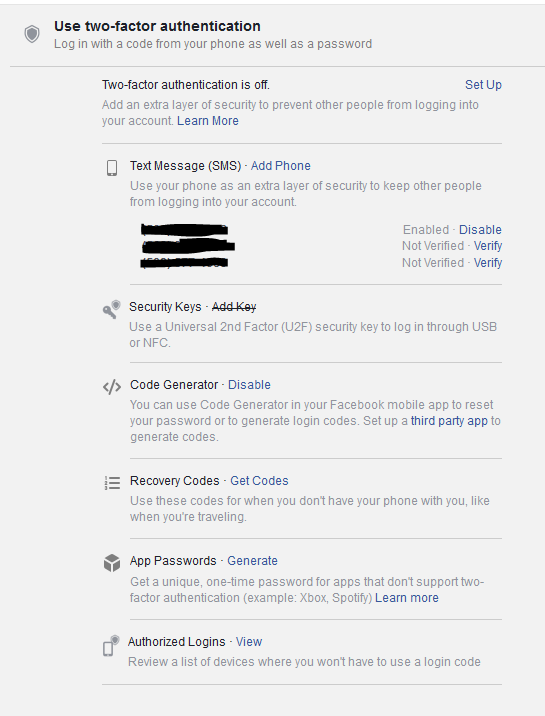
For consumers, two-factor authentication solutions are only going to get easier and less intrusive going forward. Having to enter in an SMS code only takes a few second and dramatically reduces your exposure. Over time, biometrics will start to become more commonplace and will add another layer of protection.
For those who can’t wait for biometric technology to mature or who find entering SMS codes too tedious, a better alternative could be an authenticator app on your phone that eliminates the need to enter a code. Google and Microsoft now offer apps and a number of others are available for Android and iOS including Twilio Authy, Duo Mobile and LastPass Authenticator. Most of these apps work the same. Set up the app and it then produces a rotating set of codes that you can use whenever needed. More than 10,000 websites and apps offer support for authenticator apps.
Another convenient way to set up and start using 2FA is with a <$20 U2F security token. U2F is a new standard for universal two-factor authentication tokens. These tokens can use USB, NFC, or Bluetooth to provide two-factor authentication across a variety of services and browsers including Chrome, Firefox, and Opera for Google, Facebook, Dropbox, and GitHub accounts and much more. When you insert the token in your computer’s USB port or tap it against your phone, the browser communicates with the token using secure encryption technology and provides the correct response that lets you log into a website. All very convenient, but make sure not to lose that token!
For business applications, two-factor authentication is a must, especially for any user accounts that have access to sensitive applications or customer information. Onboarding and deploying two-factor authentication is a major challenge for any organization. Automating and integrating two-factor authentication technology in applications and services takes effort but is also a vital step to guarding against security breaches.
In future posts, I will look at what’s involved with setting up 2FA for a business among other topics related to securing business information.
